Overview
The foundation of various businesses' digital transitions is the Application Programmable Interface (API). The importance of APIs in the workplace is growing, whether used to build applications in new cloud-native micro service and server less architectures, automate business-to-business activities, or act as a back end for mobile applications. Unfortunately, cybercriminals are aware of this move towards an API-centric world and are developing new attack methods at a rate equal to the rate of API expansion. Therefore, businesses urgently need to implement new security measures to secure their APIs and other digital assets. Combining an API Gateway with an API Access Management system, which offers a centralized point of control with carefully monitored policies and context-aware access management, is the ideal method to secure your APIs. Organizations will be able to comprehend its specific risks, pinpoint security holes, and identify threats if a web application and API security solution is integrated into the planning, execution, or optimization of the information security strategy.
Types of Web Application Security Risks
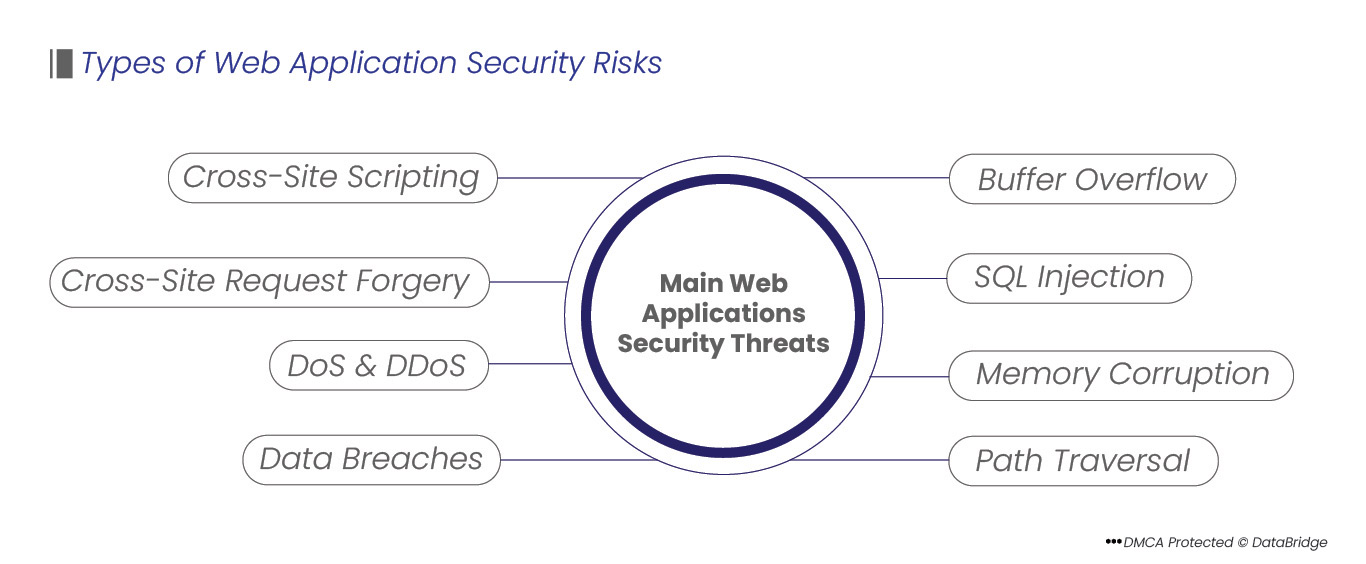
Depending on the attacker's objectives, the sort of work done by the targeted organization, and the specific security flaws in the application, different attack types may be used against web applications.
- Zero-day Flaws: These flaws have not yet been discovered by an application developer, and a fix is not yet available. Attacks aim to take advantage of these flaws as soon as possible, then frequently try to get through security providers' defenses
- SQL injection (SQi): Using SQL injection (SQi), an attacker can take advantage of flaws in the way a database processes search queries. Attackers can change or add user permissions, access unauthorized information, manipulate or delete sensitive data, and more using SQi
In July 2022, a severe SQL injection problem affecting SonicWall's GMS (Global Management System) and Analytics On-Prem products was recently made public in a security advisory. The bug has a 9.4 critical rating and is tracked as CVE-2022-22280. Owing to this vulnerability's minimal attack complexity and tremendous harm potential, anyone with a basic understanding of SQL injection can exploit it. There is no need for user interaction or authentication to use CVE-2022-22280 from the network.
- Cross-site scripting (XSS): It is a security flaw that enables an attacker to insert client-side scripts into a webpage to get direct access to crucial information, pass as the user, or fool the user into disclosing crucial information
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks: Attackers can use several different vectors to flood a targeted server or the infrastructure around it with various kinds of attack traffic. A server starts to act sluggishly and eventually refuses service to incoming requests from genuine users when it can no longer efficiently handle incoming requests
According to Check Point's "Threat Intelligence Report 2023," a single Indian firm saw 2,146 cyberattacks on average per week during the past six months, as opposed to 1,239 attacks per organization internationally. With the faster deployment of digital platforms, applications, and environments for remote work from home that COVID-19 brought about, DDoS attacks increased globally. Geopolitical crises, namely Russia's war against Ukraine and its NATO allies, are also associated with a significant increase in DDoS assaults, particularly on the healthcare, power and utilities, and logistical and supply chains sectors. These increased DDoS attacks are aimed at the adversaries' essential infrastructure.
Comcast Business stated in a 2022 report that it successfully stopped 24,845 multi-vector DDoS assaults in 2021, a 47% increase over 2020. In 2021, 69% of Comcast's clients experienced DDoS attacks, and 55% of those were multi-vector attack targets.
The global distributed denial of service market has witnessed substantial growth in recent years due to the increase in DDoS threats across IoT environments. In addition, the upsurge in multi-vector DDoS attacks and rising demand for cloud-based and hybrid DDoS protection and mitigation solutions are also considered to be the major factors enhancing the growth in the forecast period.
To learn more about the study, visit: https://www.databridgemarketresearch.com/reports/global-distributed-denial-of-service-market
- API Abuse: Software that enables two apps to connect is known as an API, or application programming interface. Like any sort of software, they might include flaws that let hackers insert nefarious code into a particular program or snoop on private information as it is transferred between applications. As API usage rises, this attack type is becoming more prevalent
- Abuse of third-party Code: Modern web applications frequently use a wide range of third-party tools. One example is a [e-commerce site] using a third-party payment processing service. If an attacker discovers a flaw in one of these tools, they may be able to steal the data it processes, stop it from working, or exploit it to introduce malicious code into other parts of the application. This attack class includes magecart assaults, which steal credit card information from payment processors. These assaults are sometimes referred to as supply chain attacks on browsers
- Page Scraping: Attackers may also use bots to scrape substantial content from websites. They might use this information to undercut a rival's prices, impersonate the page owner for evil, or other objectives
- Memory Corruption: Memory corruption is the unintended modification of a memory location, which might cause the software to behave unexpectedly. Bad actors will try to detect memory corruption and use exploits such as code injection or buffer overflow attacks to their advantage
- Buffer overflow: A software anomaly known as a buffer arises when data is written to a designated area of memory. Data is rewritten in nearby memory regions when the buffer reaches its limit. This behavior can be used to inject malicious code into the target machine's memory, perhaps leading to a vulnerability
In August 2023, Ivanti Avalanche, an enterprise mobility management (EMM) tool created to manage, watch over, and secure various mobile devices, is affected by two stack-based buffer overflows jointly tagged as CVE-2023-32560. The vulnerabilities are remotely exploitable without user authentication and are classified as critical (CVSS v3: 9.8), allowing attackers to run arbitrary code on the target system
- CSRF (cross-site request forgery): Cross-site request forgery is accomplished by deceiving a victim into sending a request using their authentication or authorization. An attacker can send a request pretending to be a user by using the user's account rights. Once an attacker has gained access to a user's account, they can exfiltrate, delete, or alter sensitive data. Targets frequently include highly protected accounts such as administrators or executives
- Credential Stuffing: Attackers may use bots to swiftly enter a huge number of stolen username and password combinations into an online application's login portals. This is known as "credential stuffing." If the attacker can access a real user's account due to this practice, they may steal the user's data or carry out fraudulent transactions using the user's name
- Attack Surface Misconfigurations: The servers, devices, SaaS, and cloud assets that are accessible through the Internet make up an organization's whole IT footprint, which is susceptible to cyberattacks. An attack surface can continue to be vulnerable by omitting or configuring some components
Strategies for Web Application Security
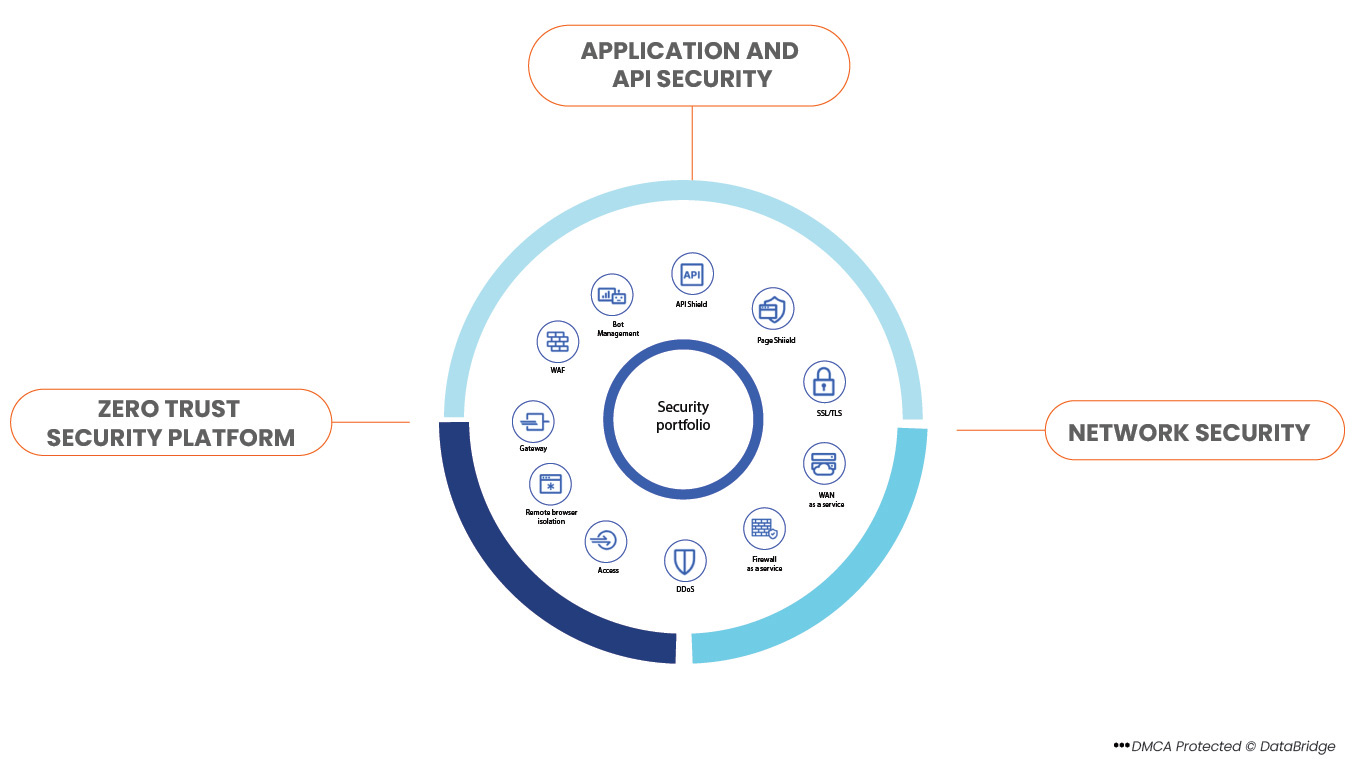
- DDoS mitigation: DDoS mitigation services use specialized filters and highly high bandwidth capacity to stand between a server and the public Internet, keeping surges of malicious traffic from swamping the server. These services are critical since several contemporary DDoS assaults generate sufficient malicious traffic to swamp even the most resilient servers
- Bot management: This technique separates automated traffic from human users and forbids the former from accessing a web application using machine learning and other specialized detection techniques
The botnet detection market has witnessed substantial growth in recent years owing to the growing utilization of APIs across several online businesses, namely gaming, e—commerce and others. Thus, continuously monitoring API requests, implementing zero-trust architecture, and deploying instant bad bot mitigation techniques are a few ways to protect APIs from bots attcks.
According to the Data Bridge Market Research analysis, the market for global botnet detection market is projected to grow at a compound annual growth rate (CAGR) of 38.30% from 2022 to 2029.
To learn more about the study, visit: https://www.databridgemarketresearch.com/reports/global-botnet-detection-market
- Web Application Firewalls (WAF): These devices block traffic known to exploit known or suspected to exploit web application vulnerabilities. The rapid and stealthy emergence of new vulnerabilities makes WAFs crucial because almost no organization can detect them on its own
- Management of the SSL/TLS encryption process's essential components, such as creating private keys, renewing certificates, and revoking certificates because of flaws by a third party. This eliminates the chance that certain components will be missed and expose confidential traffic
- API Gateways: These tools can find omitted "shadow APIs" and stop traffic that is known or believed to be aimed at exploiting API vulnerabilities. They aid in managing and keeping track of API traffic
The application programming interfaces (API) management market has witnessed substantial growth in recent years owing to the rising need for APIs to enhace digital transformation and the development of hybrid and multi-cloud API Management for enterprises to meet user demand, which will further supplement the market growth in the forecast period. According to the Data Bridge Market Research analysis, the market for global predictive analytics market is projected to grow at a compound annual growth rate (CAGR) of 31.05% from 2023 to 2030.
To learn more about the study, visit: https://www.databridgemarketresearch.com/reports/global-api-management-market
- DNSSEC: A technology that ensures DNS communication for a web application is appropriately directed to the right servers, protecting users from being intercepted by an on-path attacker
- Client-Side Security: This helps organizations detect malicious behavior earlier by checking for new third-party JavaScript dependencies and changes to third-party code
- Attack Surface Management: Use one location to map your attack surface, find potential security issues, and quickly mitigate those risks using actionable attack surface management tools
Ideal Practices for Application Security for Different Businesses
- Supplying Secure Authorization and Authentication: Strong password security rules built in and enforced, choices for multi-factor authentication that include hard keys, access control features, and other procedures make it more difficult for attackers to get unauthorized access to user accounts and move laterally within your application
- Requiring Input Validation: Preventing harmful code from entering the application through an injection attack by preventing incorrectly formatted data from being processed by the application's workflows
- Utilizing the Most Recent Encryption Techniques: Storing user data in an encrypted format and utilizing HTTPS to encrypt the transmission of both inbound and outbound traffic both assist in preventing data theft by hackers
- Coding Change Documentation: This enables security and development teams to address newly discovered vulnerabilities quickly
- Monitoring APIs: There are tools for finding ' shadow APIs' that have gone unnoticed but could be an attack surface; however, API security is made simpler if APIs are never missed in the first place
Utilization of Critical Security Controls (CIS) Services in Different Industries
Businesses from many industries, including those with strict regulations, can use Bot Management and other Cloudflare-powered CIS products to meet security, performance, and resilience demands. For instance:
- Healthcare – According to IBM Cost of a Data Breach Report, the average cost of a data breach in the healthcare sector climbed from USD 10.10 million in 2022 to USD 10.93 million in 2023, which is a rise of 8.2%. CIS services are even more essential to help in stopping these expensive attacks because healthcare has the greatest cost per data breach for the thirteenth consecutive year. Healthcare clients can use the combination of CIS DDoS, WAF, and Bot Management to help mitigate against sophisticated malware bot attacks
- Financial Services - Banks and other financial institutions can employ CIS services such as DDoS mitigation and Web Application Firewall (WAF) to address security issues. Customers can defend their Internet-facing apps against various exploits, including day-zero attacks, by utilizing the turn-key Web Application Firewall (WAF) policies.
- eCommerce - The rising use of APIs in eCommerce has also raised the possibility of security problems with APIs. API gateways can be safeguarded by eCommerce organizations using CIS services for DDoS protection
- Higher Education - Large amounts of data on all students, professors, and alumni are hosted by educational organizations across their extensive networks, particularly higher education institutions. Cybercriminals can then use this data to further their assaults on specific targets or larger-scale schemes against institutions as a whole
- Construction – The construction business is plagued by "phishing-prone" workers. The type of data that the building industry gathers serves as the inspiration for such attacks. Cyber attackers are interested in personal data and valuable information such as business secrets, building schedules, cost estimates, and project bids, among others. The stolen business information may result in serious injury and financial loss. The CIS control framework addresses problems and weaknesses that exist in the sector
- Automotive - The automobile industry today sees connected and autonomous vehicles as intelligent machines that collect copious amounts of telemetry data. This industry has a motive to look more closely at API security because of vulnerability leaks and API-based proof of concept exploits
- Small- to Medium-Sized Companies don't represent an industry as they can belong to any subcategories. While it might seem logical that hackers would be less drawn to smaller 'organizations' relatively less valuable assets than larger businesses, this is far from the case. According to Verizon data, small firms have been engaged in a startling 28% of all data breaches in 2020. Small firms frequently have less money and process less data than major enterprises, but they also have less reliable security solutions. Furthermore, many small enterprises have scant or no cybersecurity in place.
Strategic Initiatives Taken by Different Companies
- In August 2023, Cloudflare stated that IBM Cloud Internet Services (CIS), powered by Cloudflare, has increased the range of services it offers, including Cloudflare Bot Management, which is now accessible to businesses on the Enterprise Premier Plan to help them address and counteract the growing threat posed by harmful bot traffic
- In June 2023, SecureIQLab, a provider of cloud validation, released its third Web Application Firewall (WAF 3.0) testing iteration. The first-of-their-kind API security test cases will be included in this version. Market-leading security solutions will be assessed by WAF 3.0 for their ability to survive today's complex cyber threat scenario
- In May 2023, Radware unveiled a new Cloud Web DDoS Protection solution. Modern DDoS mitigation techniques are being outpaced by a new breed of more aggressive layer 7 (L7) HTTPS Flood attacks, commonly referred to as Web DDoS Tsunami attacks. This approach is intended to close this gap. It minimizes false positives and offers wide attack coverage against zero-day attacks and most advanced attacks
- In April 2023, Edgio came up with an advanced bot management that provides observability into good bots while proactively mitigating a variety of emerging bad bots. Advanced Bot Manager uses machine learning to identify bots based on signature and behavioral fingerprinting, leveraging the vast volumes of data continuously collected from the platform's large global deployment. In order to analyze all traffic for bots in real-time across the whole Edgio global network, the solution runs natively on every server
- In October 2022, Akamai launched a distributed denial-of-service (DDoS) protection solution named Prolexic, a new sixth-generation platform. It is a totally software-defined, high-performance, scalable architecture that improves the capacity to meet changing consumer needs and upcoming cybersecurity requirements
Conclusion
As businesses migrate to the cloud, enabling the digitization of massive data sets, services, and goods, API security will become increasingly crucial in 2023 and beyond. With this change, the attack surface of vulnerable APIs increases, necessitating the need to harden API services to safeguard business operations, clients, and data. Within the cybersecurity community and for many organizations, API security is moving up the priority list. API security is now a very crucial issue since exposed or improperly configured APIs give an excellent chance for threat actors to infiltrate a network.

